Configuring Identity Providers in Azure B2B
Suppose your organization has an Azure AD tenant, and that you need to collaborate with users outside your organization - these could be partners, clients, suppliers, volunteers, etc. In these circumstances, you may want them to have access to certain internal resources and apps; Azure B2B is optimal for this kind of collaboration, as its External Identities feature allows you to moderate who has access, and how they can obtain it.
Intro to Azure AD External Identities
Azure AD External Identities refers to all the various ways you can securely interact with these external users, while allowing them to employ Azure's bring-your-own-identity feature. In this article, we will walk through how these External Users are configured in your Azure AD B2B tenant, and how to configure External Identities to access all its benefits.
In Azure B2B, guest (external) users may have their own Azure AD account; it could be a Microsoft account, a social account like Google or Facebook, a federated account such as SAML or WS-Fed, or an alternative email account with a one-time passcode that authenticates them at each sign-in. Each of these login types is added into your regular Azure AD tenant, where they exist as guest users and can access your Office 365 apps, SaaS apps, and line-of-business apps.
To enable conditional access, MFA, identity protection, and other security features, you can also license external users with P1 or P2 licenses.
Identity Providers
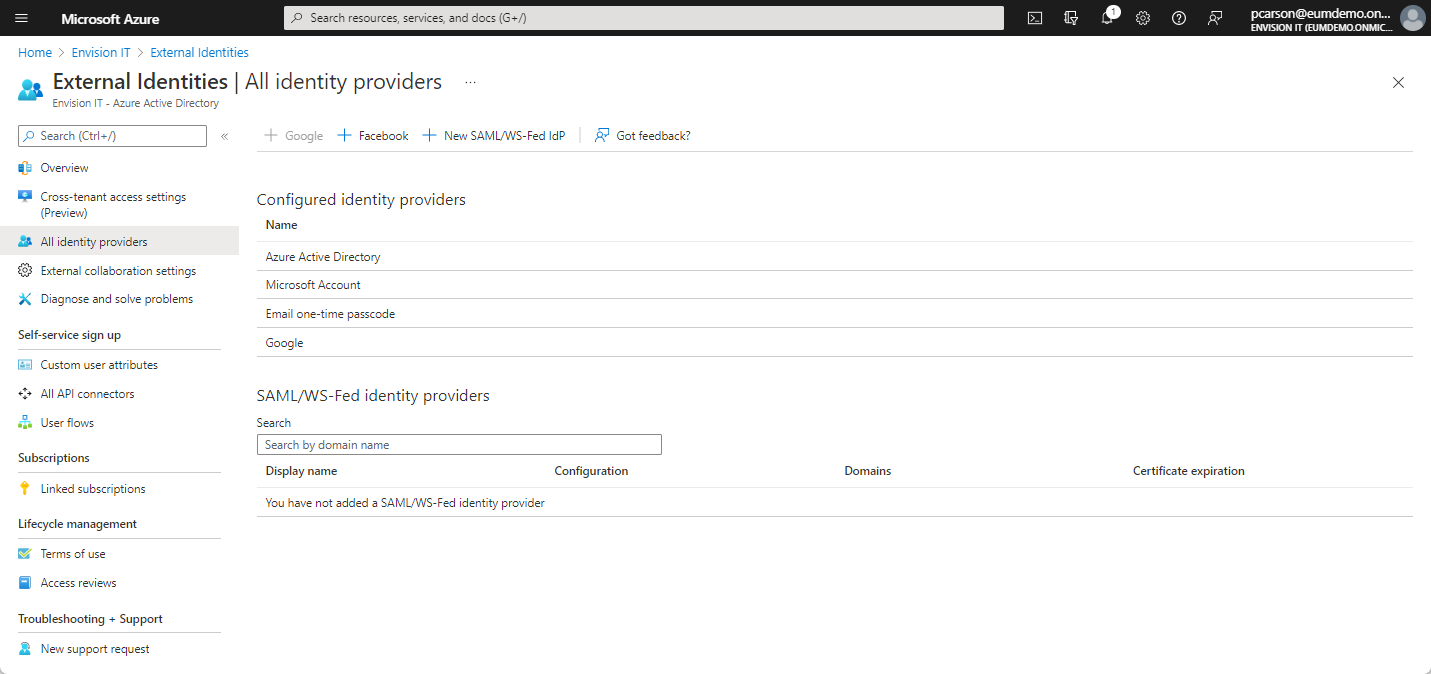
One useful feature of Azure AD External Identities is this concept of Identity Providers, which are essentially the different login types that users can choose that will authenticate their identities when they are accessing your tenant. Opening External Identities > All Identity Providers in the navigation bar of your Azure portal, you can add, edit, or remove approved identities in your tenant while simultaneously providing authentication services. For external users who already have an Azure AD or Microsoft account (MSA), logging in to your tenant happens automatically as they are already authenticated in Azure AD. Guests coming from other identity providers will require some additional configuring in External Identities. This section will discuss the setup required for guest users that use identity providers besides Azure AD/MSA.
Email One-Time Passcode
In this scenario, when a guest user tries to access an organization's shared resource with their preferred email, they can receive a one-time passcode (OTP) directly to their email inbox; this passcode is used to validate that the user still owns that email address, and allows them to continue signing in. Typically, the OTP is valid for a fixed amount of time and can only be used once. At Extranet User Manager, we have seen that many users leverage OTP with success.
In the image below, the external user is being prompted to receive a one-time passcode to their email to authenticate their identity.
.png)
Once the passcode is retrieved from the user's email, they must use it to continue signing in. After 30 minutes, the passcode will expire and a new one must be requested. This process is repeated every time the user signs in.
.png)
For a walkthrough on how to set up Email OTP as an approved identity provider in your Azure AD, refer to the following Microsoft documentation: One-time passcode authentication.
Google federation is an approved identity provider that allows users to access email invitations by signing in through their Google apps. In this scenario, the guest user will be prompted to sign in to Google and will automatically be redirected to your shared resources/apps. The situation is similar to that of a Microsoft 365 account holder. This login experience is only available to Gmail account holders; that said, it is useful to note that individuals with Google Workspace domains must use a SAML/WS-Fed identity provider instead.
The sign-in process with a Google identity provider starts off with the user entering their Gmail address.
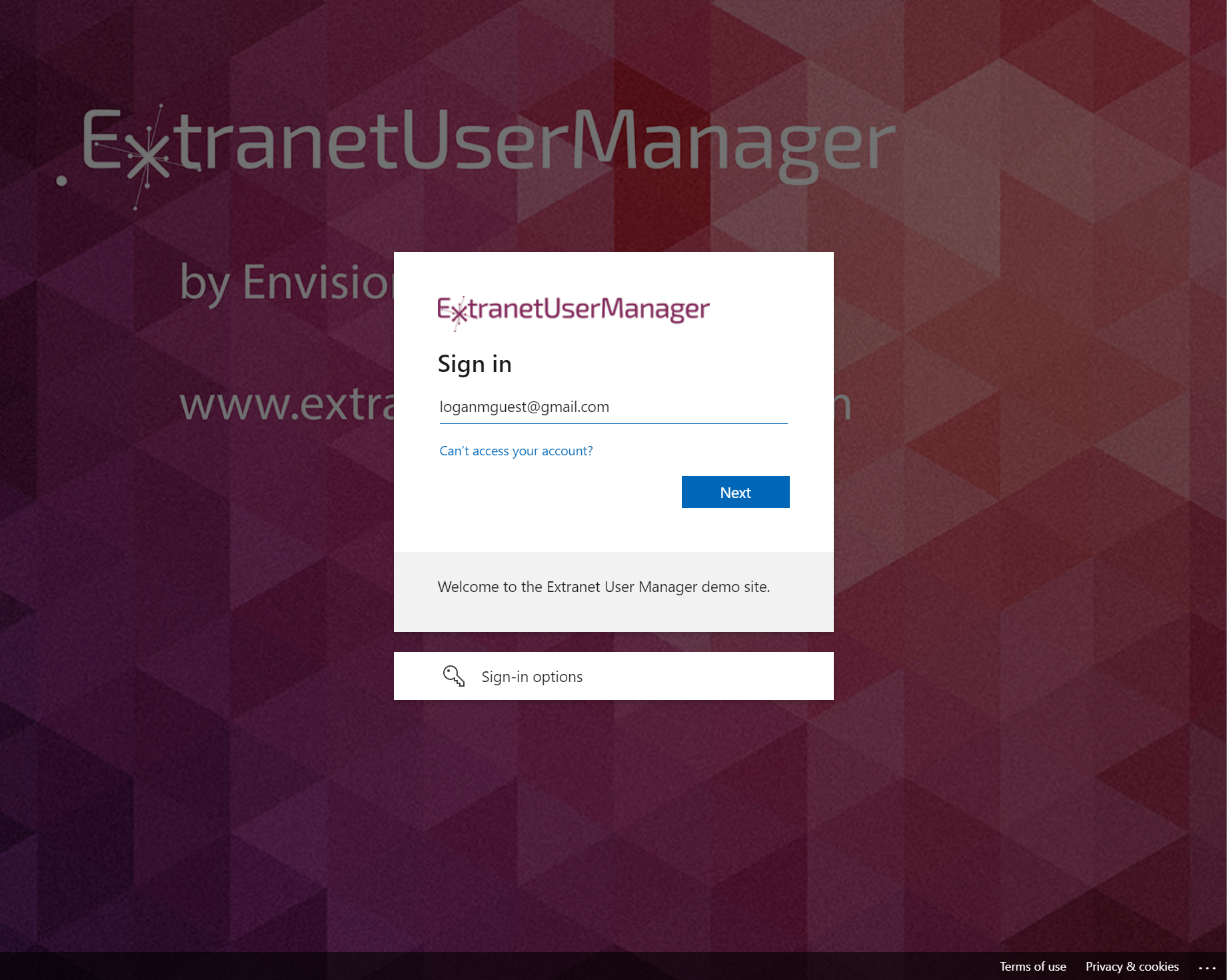
The user is then redirected to their Google login page, where they must sign in with their existing credentials in order to proceed.
.png)
Once the user has successfully logged into their Google account, they are redirected to the organization's login page, as shown in the image below.
.png)
Learn more about how to set up federation with Google by accessing the following Microsoft document: Add Google as an identity provider for B2B guest users.
Using Facebook as an identity provider requires some extra setup effort. You will need to set up a Facebook account to access the Facebook developers console and create a new application, which will then generate an App ID and a secret. Back in Azure AD, you would click on the + Facebook key and enter the ID and secret where prompted on the right-hand side, highlighted in the image below.
An in-depth walkthrough on how to set up Facebook as an identity provider can be found in the following Microsoft document at: Add Facebook as an identity provider for External Identities.
An important limitation to note is that SAML/WS-Fed IdPs cannot be used in your self-service sign-up user flows. However, you can still set up a federation with such IdPs so that they can sign in to your apps/resources using their preferred accounts. Guest users redeem an email invitation from your organization, which redirects them to their IdP to continue signing in before they land wherever your shared resources are stored.
Recently, Microsoft announced that they no longer support an allow list of IdPs for new SAML/WS-Fed IdP federations. As of right now, you can only add one domain to your external domain - this may be increased in the future. To learn about the requirements and limitations for setting up a SAML/WS-Fed federation, refer to the Microsoft document Federation with a SAML/WS-Fed identity providers for guest users.
Managing External Users
In order to manage your guest users and see which identity providers they are using, go back into the Azure AD home and click on Users > All Users in the navigation bar. Here, you can filter by User Type and see what identity provider they are using under “Identity Issuer”, as well as how they were added to the tenant under “Creation Type”.
Upcoming Events
Interested in learning more about how to leverage External Identities to its fullest potential? Click the link below to register for our upcoming webinar, surrounding best practices in Azure AD B2B and guest management:
Azure B2B and Guest Management Best Practices
Latest Articles
Related Pages
{{{hyperlink RelativeURL Title Title null}}}
{{#if EventStartDate}}{{eventDate EventStartDate EventEndDate}}
{{/if}} {{#if PublishedDate1}}{{generalDate PublishedDate1}}
{{/if}} {{#if RollupContent}}{{{RollupContent}}}
{{/if}}{{{hyperlink RelativeURL Title "Read more..." null}}}